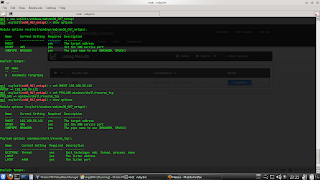
Make fuzzer then run after
clicking attach program in OllyDbg.
Fuzzer sends a buffer of 2500
bytes to the application
The crash occurred on the
application, but registrer EIP not affected by the buffer. If you
want to see in the SEH then select the view and select SEH chain.
Press shift + f9, and now the
value of EIP changed.
If you see in the column
below it looks buffers sent using fuzzer into the stack. To view the
data residing on memory application, right-click the line and select
Follow in the stack dump.
^_____^